How do I setup integration with Jira?
You can integrate and send tickets directly into Jira. This allows for quicker and easier management of your vulnerabilities. The ticket status will be updated automatically in Jira.
Jira On-premise prerequisites
To be able to set up an integration with your on-premise Jira, you will need to whitelist our production networks so that the Security Center can communicate with Jira:
- IPv4: 185.163.84.0/22
If /22 is too large to grant access, then use the following:
185.163.84.0/24 and 185.163.85.0/24 - IPv6: 2a0b:6800::/29 (optional)
Integration setup
To integrate Holm Security with Jira, follow the steps below.
- Log in to Security Center.
- Click on the Menu Icon in the top right corner.
- Click Settings > Integrations.
- Enable Jira by checking the checkbox.
- Enter your Jira cloud credentials:
- Username
- API token
- Jira URL
- Ticket naming
- Click Connect to Jira.
- Once connected, two drop downs will appear, allowing you to connect the integration with "Project" and "Issue type."
- Click OK.
- Click Remediation > Setup.
- Check Enable Jira notifications.
- Click OK.
- Done!
Priority fields
Make sure that the priority field is added to every new issue type. The field should be added under the context field and to the Create Screen of that issue type. See the images below:
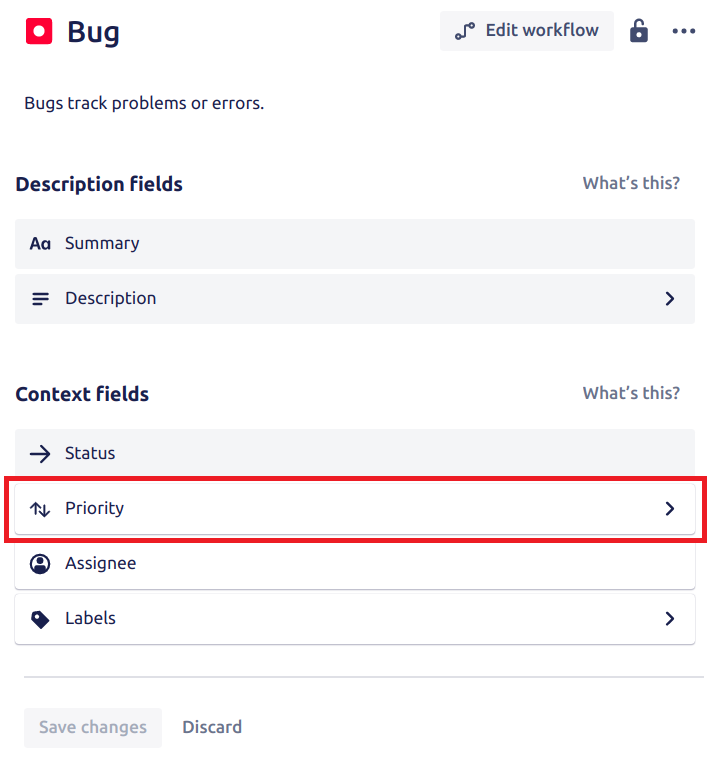
-png.png?width=800&height=803&name=image%20(20)-png.png)
Make sure only to use the fields available in the JIRA UI if you create a ticket of the same type. Use the correct fields that belong to the issue type.
Ticket status update
The task status automatically synchronizes between the Vulnerability Manager and the remediation module. If our scanner detects a vulnerability no longer exists, it will close the ticket with a "fixed" status in both the Remediation module and the Jira system.
Example scenario
- The scanner detected vulnerability, which was reported in Vulnerability Manager.
- After the security engineer confirms the vulnerability, they can create a ticket from Security Center. This ticket will be generated in the Remediation module and Jira, including all the necessary details and descriptions.
- The responsible individual takes action to fix the vulnerability.
- The scan is rerun, either manually or by schedule.
- The scanner checks if the vulnerability that was identified earlier still exists. If the vulnerability is no longer present, the ticket is closed in both the Jira system and the remediation module.