- Knowledge base
- Cloud Security
- Google Cloud Platform (GCP)
-
Security updates
-
Product news
-
Next-Gen Vulnerability Management
-
Getting started
-
General
-
Operating status
-
Network & System Security
-
Web Application Security
-
Cloud Security
-
API Security
-
Phishing Simulation & Awareness Training
-
Attack Surface Management
-
Scanner Appliance
-
Device Agent
-
On-premise platform deployment
-
Asset management
-
Vulnerability manager
-
Reports
-
Digest reports
-
Organizer
-
Continuous monitoring
-
Integrations
-
Platform API
-
Remediation
-
Users
-
PCI DSS ASV scans
-
Terms & conditions
-
Dashboard
Where do I find my Google Cloud credentials?
To scan Google Cloud, the following IDs from your account are required:
- Project
- Client email
- Private key
To find these requirements within your Google Cloud environment, please do the following:
- Log into your Google Cloud console and activate your Cloud Shell.
- Create a new file called "holm-security-cloud-scan.yaml". You can use this command:
nano holm-security-cloud-scan.yaml - Copy and paste the following YAML code in the file on your Cloud Shell, press Ctrl + X, and type Y to save the file.
name: roles/HolmSecurityAudit
title: Holm Security Audit
includedPermissions:
- cloudasset.assets.listResource
- cloudkms.cryptoKeys.list
- cloudkms.keyRings.list
- cloudsql.instances.list
- cloudsql.users.list
- compute.autoscalers.list
- compute.backendServices.list
- compute.disks.list
- compute.firewalls.list
- compute.healthChecks.list
- compute.instanceGroups.list
- compute.instances.getIamPolicy
- compute.instances.list
- compute.networks.list
- compute.projects.get
- compute.securityPolicies.list
- compute.subnetworks.list
- compute.targetHttpProxies.list
- container.clusters.list
- dns.managedZones.list
- iam.serviceAccountKeys.list
- iam.serviceAccounts.list
- logging.logMetrics.list
- logging.sinks.list
- monitoring.alertPolicies.list
- resourcemanager.folders.get
- resourcemanager.folders.getIamPolicy
- resourcemanager.folders.list
- resourcemanager.hierarchyNodes.listTagBindings
- resourcemanager.organizations.get
- resourcemanager.organizations.getIamPolicy
- resourcemanager.projects.get
- resourcemanager.projects.getIamPolicy
- resourcemanager.projects.list
- resourcemanager.resourceTagBindings.list
- resourcemanager.tagKeys.get
- resourcemanager.tagKeys.getIamPolicy
- resourcemanager.tagKeys.list
- resourcemanager.tagValues.get
- resourcemanager.tagValues.getIamPolicy
- resourcemanager.tagValues.list
- storage.buckets.getIamPolicy
- storage.buckets.list
stage: GA - Run the following command to create the role; use your Organization ID to create the role at the Org Level: `gcloud iam roles create HolmMSecurityAudit --organization=YOUR_ORGANIZATION_ID --file=holm-security-cloud-scan.yaml`
Create a Service Account
Now, you will need to create a Service Account following these steps.
- Log into your Google Cloud console and navigate to IAM Admin > Service Accounts.
- Click on Create Service Account.
- Enter "HolmSecurity" in the "Service account name", then enter "HolmSecurity API Access" in the description.
- Click on Continue.
- Select the role: Custom > Holm Security Audit.
- Click on Continue.
- Click on Create Key.
- Leave the default JSON selected.
- Click on Create.
- The key will be downloaded to your machine.
- Open the JSON key file in a text editor, copy the Project ID, Client Email, and Private Key values, and paste it into the Authentication section of Holm Security Cloud Scan Configuration window.
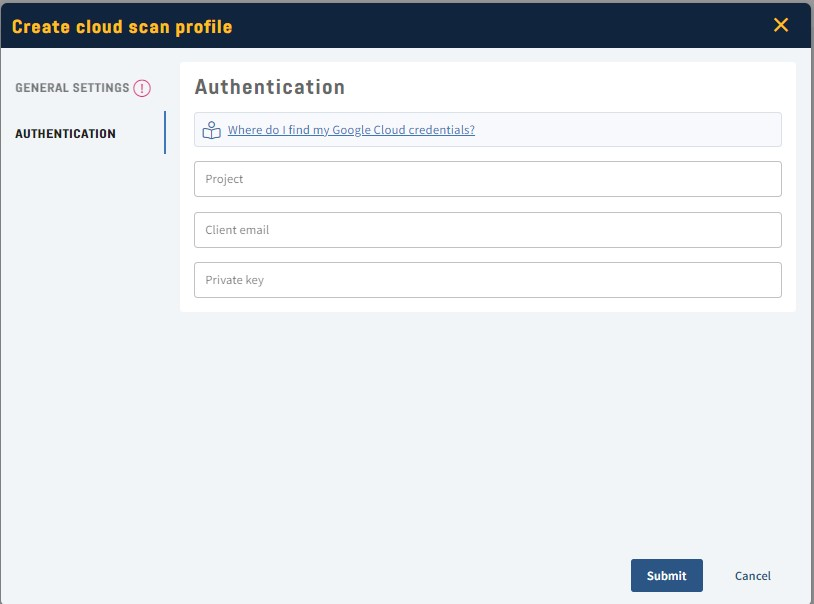
- Click on Submit.
- Done!
