How do I detect Microsoft Outlook 2013/2016 Privilege Escalation Vulnerability?
Information about the Microsoft Outlook 2013/2016 Privilege Escalation Vulnerability (CVE-2023-23397)
CVE-2023-23397 is a privilege escalation vulnerability actively exploited in the wild.
This vulnerability allows a remote and unauthenticated attacker to retrieve the victim's credentials just by sending a specially-formatted appointment to the user, which triggers automatically when it is retrieved and processed by the Outlook client without any user interaction.
The successful exploitation of this vulnerability allows an attacker to obtain the victim's hashed NTLM credentials and use them to authenticate as the victim to other systems that support NTLM authentication.
To check if your systems are affected by the Microsoft Outlook vulnerability
CVE-2023-23397, you will need to run an Authenticated Network Scan using
Holm Security VMP.
You will find detailed information about setting up your authenticated scanning
profile in this article: https://support.holmsecurity.com/hc/en-us/articles/212841809
And you can find more information in this section:
https://support.holmsecurity.com/knowledge/system-network-scanning#authenticated-network-scans
If your system is vulnerable, you will find one of the following HIDs in your
generated scan report:
- HID-2-1-5349142
To scan for this vulnerability specifically, please do the following:
- log in to your Security Center
- Click on Scan Network > Scans
- Click on Scan profile.
- Click Create Scan Profile.
- Name the profile under General Settings and choose Basic Scan.
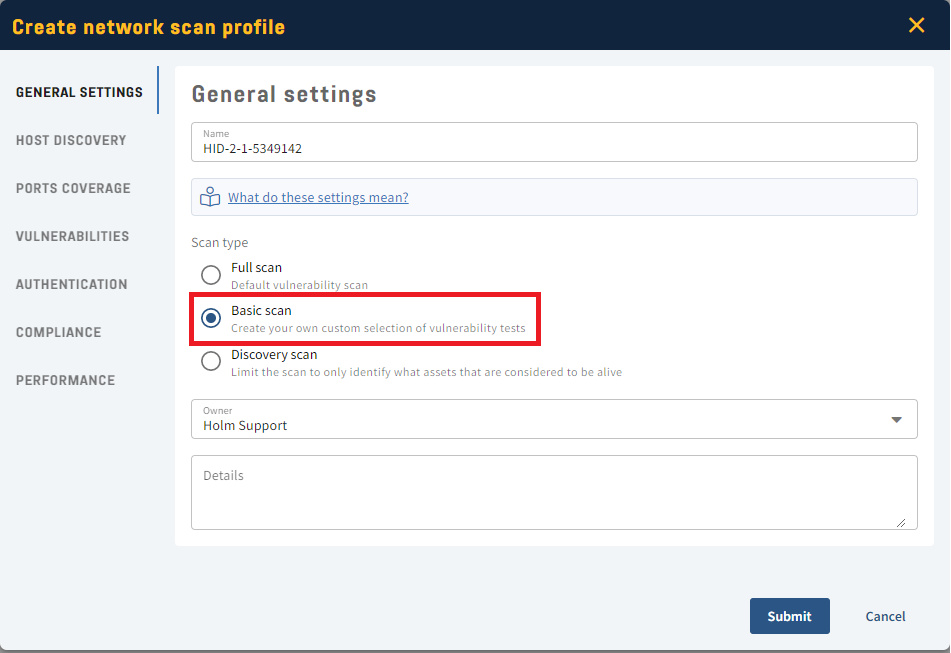
- Head to Vulnerabilities.
- Under Include type in the Vulnerability HID: HID-2-1-5349142.
- Head to Authentication and fill in the right credentials.
- Click Submit to save the profile
- Now click on Scans > Add new scan > Network scan > Vulnerability scan.
- Name your scan under General Settings and choose the pre-created profile.
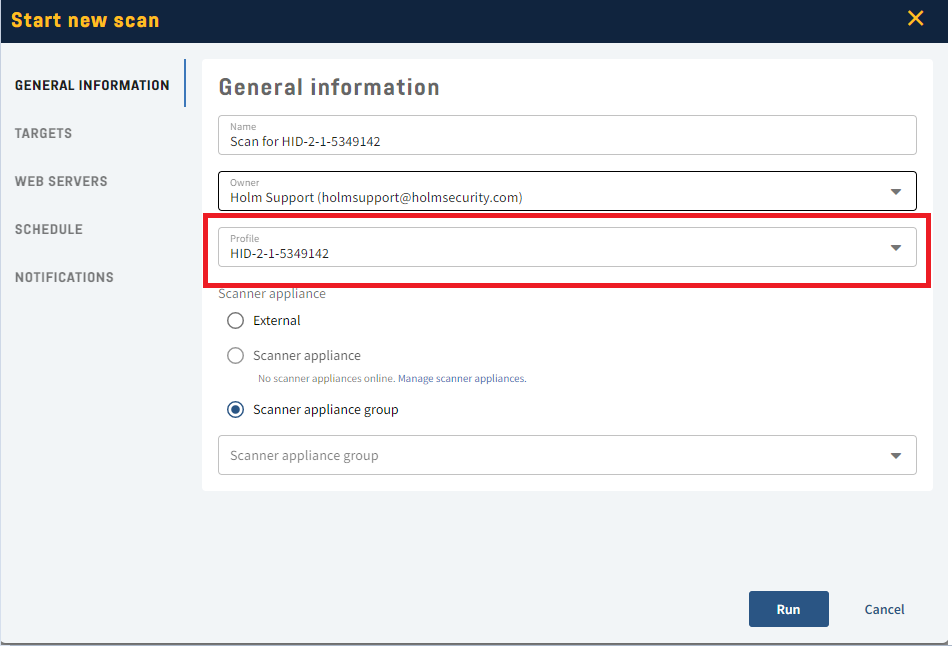
- Head to Targets and choose the target for your scan.
- Click Run.
- Done!
How do the scripts work?
In our script, we verify the installed version of Microsoft Outlook and check if it's within the vulnerable version range.