What is the difference between the OWASP Top 10 versions 2013 and 2017?
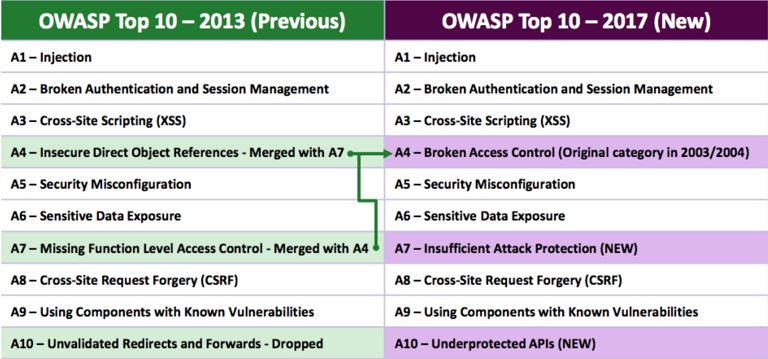
Two new risks were added with OWASP 2017
2017-A7 - Insufficient Attack Protection
Detecting, responding to, and blocking attacks makes web applications dramatically harder to exploit, yet almost no web applications or APIs have such protection. Critical vulnerabilities in both custom code and components are also discovered all the time, yet organizations frequently take weeks or even months to roll out new defenses.
2017-A10 - Underprotected APIs
Testing your APIs for vulnerabilities should be similar to testing the rest of your web application. Different types of injection, authentication, access control, encryption, configuration, and other issues can exist in APIs just as in a traditional web application.
Two items were removed from the OWASP Top 10 2017
- Cross-Site Request Forgeries (CSRFs)
- Unvalidated Redirects and Forwards
Two risks from the OWASP Top 10 2013 are merged
Insecure Direct Object References and Missing Function Level Access Control were merged into a single risk:
- Broken Access Control.